In this post I wanted to discuss the use of Citrix Enlighted Data Transport with Citrix Gateway Service. This is a feature that has been available with Citrix ADC for quite some time but it is a new feature for Gateway Service. I wanted to take you through step by step on how to configure EDT and Adaptive Transport with Gateway Service, as well as discuss any system requirements that are needed to get you up and running.
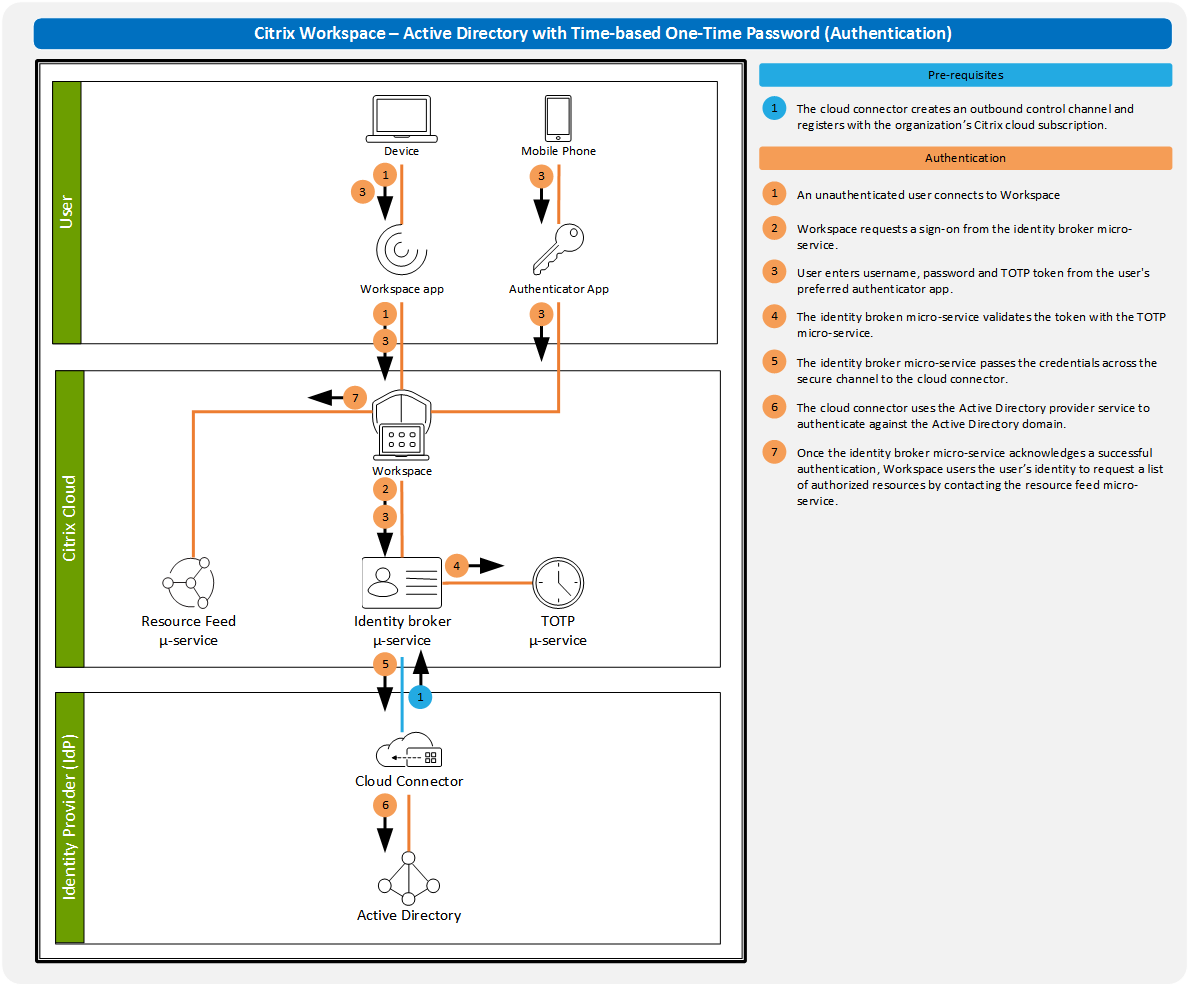
Citrix Workspace app with passthrough (Mac Domain Joined) By the end of this blog, you should have a good understanding of how with Citrix Workspace + Okta you can deliver an experience that will make your users want to use the Workspace. Citrix Workspace provides organizations with secure access to SaaS apps. In this scenario, a user authenticates to Citrix Workspace using either Active Directory or Okta as the primary user directory. Okta also provides single sign-on services for a defined set of SaaS applications.
What is Adaptive Transport
Adaptive transport is a proprietary transport protocol that functions well on highly latent networks, which TCP alone finds challenging. This protocol is adaptive and can switch to TCP or UDP based on network conditions in order to ensure the best user experience for users using HDX.
Enlighted Data Transport System requirements
- VDA 1912 or later
- Rendezvous protocol must be enabled and working ( We cover this next)
- Ports UDP 443 and TCP must be open outbound from VDA to the Internet
- Adaptive Transport must be enabled
- EDT is supported with all supported OS’s. Citrix do recommend the use of Windows 10 and Windows 2019 when running EDT with Citrix Gateway Service
- Latest Workspace App Version ( 1908 or above for Parallel connections)
Configuring Rendezvous Protocol

When you are configuring Rendezvous protocol for use with Citrix CVAD Service the following is required.
- VDA 1912 or later
- Enable the Rendezvous protocol in the Citrix policies in Studio
- The Cloud Connectors must obtain the VDA’s FQDN when brokering a session. This can be achieved by using the the following commands in Powershell:
- asnp citrix*
- Get- XDAuthentication
Set the DNS Resolution to True
Set-Brokersite -DNSResolutionEnabled $True
To check that the DNS Settings are configured correctly – Type Get-Brokersite
The DNS Resolution should now be set to True.
Citrix Policy Requirements
Now that the DNS settings are complete, we need to ensure the Citrix Policies are also set for Rendezvous protocol. (The Rendezvous protocol allows HDX sessions to bypass the Citrix Cloud Connector and connect directly and securely to the Citrix Gateway service.)
Please see more detail here: https://docs.citrix.com/en-us/citrix-virtual-apps-desktops-service/hdx/rendezvous-protocol.html
To set the Citrix policy, Open Citrix Studio and create a new policy for Rendezvous protocol.

Click enable , and also enable Adaptive transport.
Citrix Workspace Okta Download
Lets also set up Session Reliability setting, as our final policy requirement. Enabling Session Reliability will allow users to automatically reconnect to Citrix sessions after a disruption.
Citrix Workspace Download
Now that Rendezvous protocol is setup, lets move on to complete the setup to allow for the use of EDT.
Open Microsoft Group Policy Manager, and create a policy that will allow for you to set the Cipher Suite for the VDA workloads. Choose Computer configuration, Network, SSL Configuration, SSL Cipher Suite Order.
Lets now check if the settings are working as expected
Within the HDX session, launch a desktop and open powershell
The transport protocols used are displayed as below when successfully using EDT
It is also possible to check via Director
This table lists the Okta group types.
| Group Type | Description |
|---|---|
| Native Okta groups | Before you connect Okta to applications or other resources, you can create groups in your Okta org. The default group Everyone contains all users in your Okta org. To manage your Okta groups, sign in to your Okta Admin Console and click Directory > Groups. |
| Active Directory groups | Active Directory (AD) is the most common source for groups. Nearly every business of significant size uses an AD instance to manage users. You can use the Okta AD Agent integrate your AD instance with Okta. Okta does not support Domain Local Groups containing members from multiple domains. Universal Security Groups with cross-domain membership are supported if there is a two-way trust established between the domains. Universal Security Groups do not support cross-forest membership. |
| LDAP groups | You can use the Okta LDAP Agent to import groups from LDAP-compliant Windows and Unix servers. |
| Application groups | Some applications have groups that you can import into Okta. The ability to import these groups depends on whether or not the groups can be accessed through an API and if the application has been integrated with Okta. These are a few of the applications that support group import:
|
